Privacy Protocols Landscape: Navigating the Web3 Privacy Sphere
Explore the Web3 privacy landscape with zkFi, bridging privacy and compliance in blockchain. Dive into innovations from DeFi to AI/ML & social platforms and learn how zkFi's solutions are transforming privacy.
In today's hyper-connected world, privacy is paramount. Imagine if your bank transactions and social media messages were visible to everyone—this exposure could make you vulnerable to misuse and exploitation. Privacy is essential for safeguarding personal data and preventing malicious actors from disrupting our lives.
The evolution of cryptography has mirrored the growth of the Internet. In the early days, simple encryption techniques protected sensitive data. As Web 2.0 emerged, online services began collecting vast amounts of personal data, raising privacy concerns. This led to privacy-enhancing technologies like encryption and ad blockers. Now, with Web3 and blockchain technology, new challenges and solutions in privacy are taking shape.
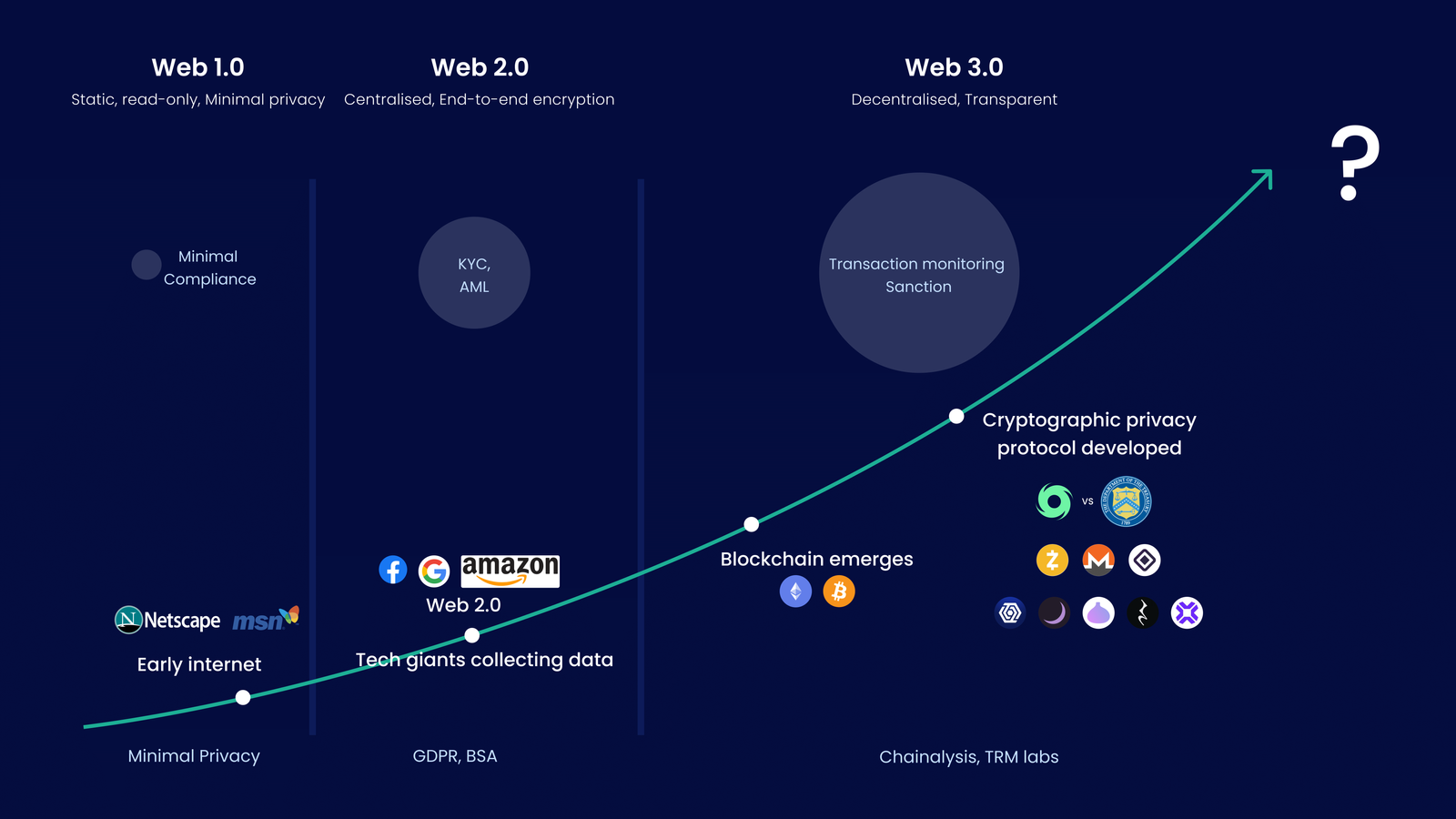
Blockchain’s decentralization, immutability, and transparency bring revolutionary benefits, but its transparency creates a significant challenge—user transactions and metadata are publicly accessible on-chain.
Popular blockchains like Bitcoin and Ethereum have this challenge. It compromises user privacy, making it vulnerable to malicious actors. Transparency allows anyone with an internet connection to see any wallet holder's full transaction history, net holdings, and user's other on-chain interactions.
For individuals, businesses, and institutions, the risk of exposing financial transactions and personal data is a roadblock to mainstream Web3 adoption.
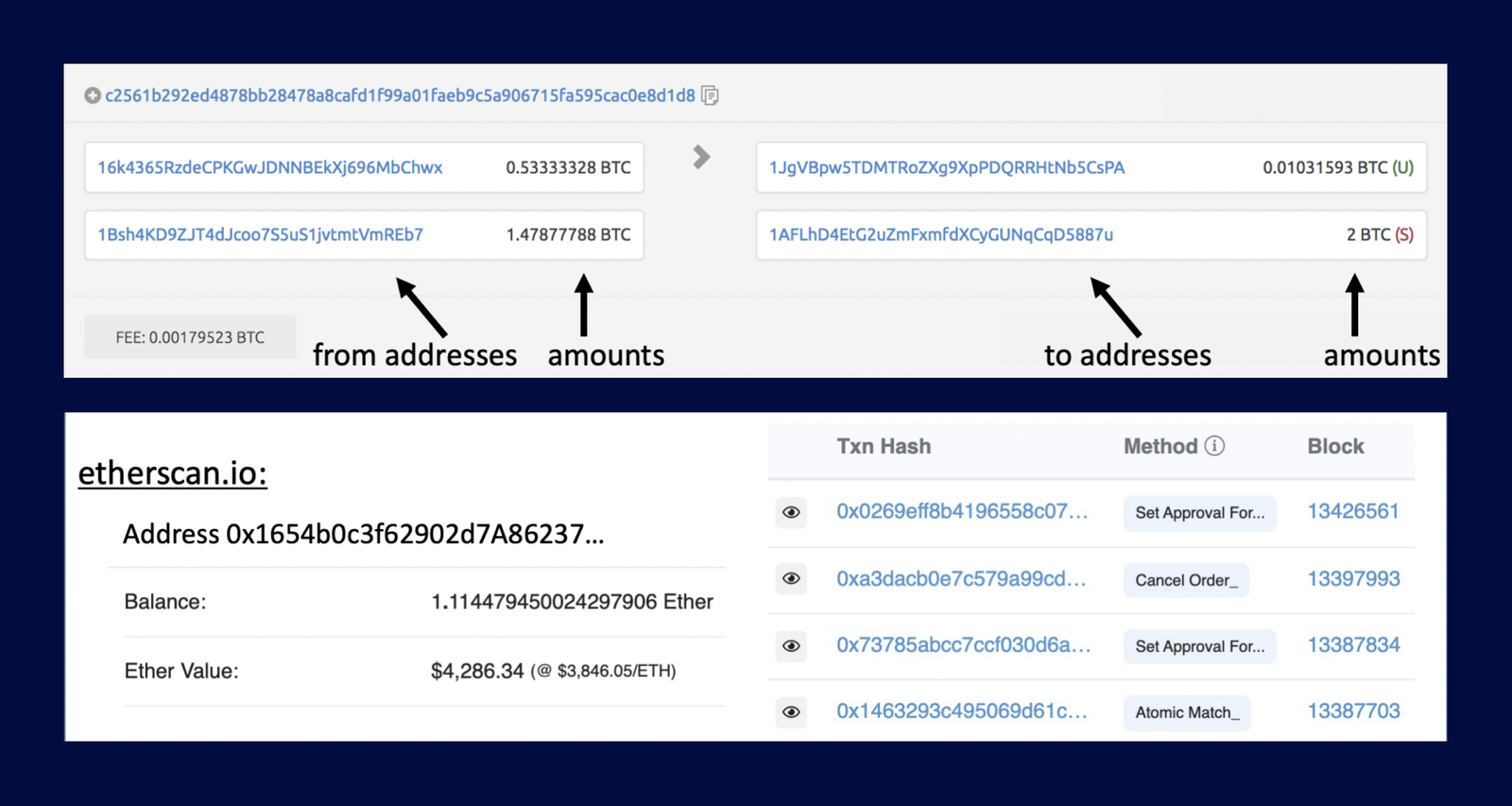
Bitcoin and Ethereum Lack Built-in Privacy
Because privacy concerns are growing, solutions like zero-knowledge proofs (ZKPs) are gaining popularity. However, most privacy tools today still have gaps. They need better compliance, easier user experiences, and broader functionality.
Let’s explore the privacy landscape and how Labyrinth provides a better solution.
Expanding Horizons of Private Transactions: From Asset to Data
The DeFi space continues to grow with various financial applications, but blockchain privacy solutions primarily focus on making transaction values private.
Beyond DeFi, we are also seeing the emergence of AI and crypto intersections with new protocols like Ritual, Bittensor, and Gensyn.
These protocols enable decentralized LLM computation to address centralized data concerns and security implications. AI agents could use crypto for payments and resource access. While these protocols solve decentralized computation issues, they do not address privacy challenges.
A New Era for Social Platforms
Social networks like Lens and Farcaster tackle the limitations of traditional social media by enabling user-owned, open social graphs that allow data portability across applications.
While these protocols empower users and creators by giving them control over their content, they still require users to compromise privacy in activities like P2P messaging or transactions within their native payment systems.
Transactions may include details such as social relationships, purchasing habits, and media usage, all of which could be misused by harmful entities. This issue becomes especially significant when user addresses are linked to real identities through KYC.
Past And Present of Privacy Protocols Design Space
Despite many efforts, no existing ZK-based privacy solution offers a comprehensive package. These solutions struggle with compliance, liquidity fragmentation, lack of compatibility with protocols, or cumbersome user experiences.
Early privacy-focused blockchains like ZCash and Monero pioneered anonymous transactions, but they were limited to peer-to-peer interactions and lacked broader applications like DeFi. Tornado Cash faced compliance challenges, while Aztec had practical limitations such as asset bridging and limited interoperability.
Aztec introduced a novel Layer 2 roll-up approach, using Plonk ZK-proofs to reduce costs and increase speed on Ethereum. However, it required users to bridge assets between chains, resulting in long waiting times. This made it impractical for many DeFi interactions, such as swaps, due to slippage risks.
Many projects face similar issues, including weak compliance guarantees and a fragmented user experience. Users hesitate to use these protocols due to concerns about asset security, compliance risks, and potential sanction-related restrictions.
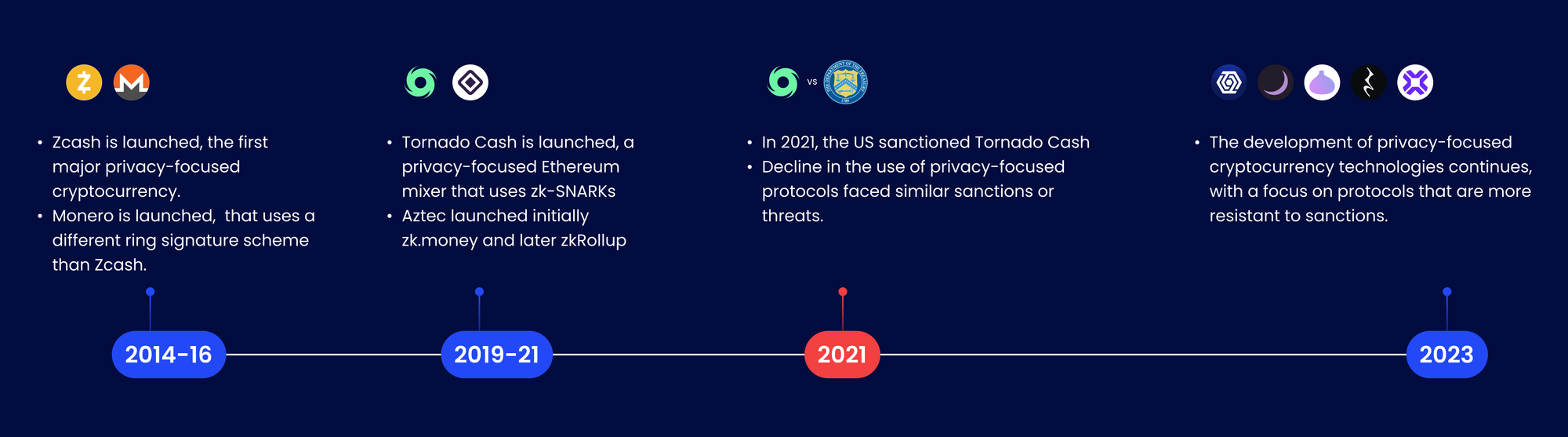
Why stand-alone privacy does not work? Learnings from Tornado Cash
Tornado Cash, an Ethereum-based mixer using zero-knowledge tools, provided anonymity by allowing users to deposit a fixed amount into a pool and later withdraw it without revealing their identity. However, its lack of compliance measures led to misuse.
In 2022, the U.S. Office of Foreign Assets Control (OFAC) sanctioned Tornado Cash, citing its involvement in laundering illicit funds, including money from the Ronin Bridge hack by North Korean hackers.
The U.S. government struggled to regulate Tornado Cash due to its anonymity and lack of compliance structures. This case highlighted the need to balance privacy with regulatory compliance in financial protocols.

Comparison of Emerging Privacy Solutions
To understand the current state of privacy protocols, we must examine their evolution. Various blockchain privacy protocols have emerged, each with strengths and weaknesses. Notable solutions include Nocturne, Elusive, Hinkal, and Silent, which each attempt to address privacy and compliance differently.
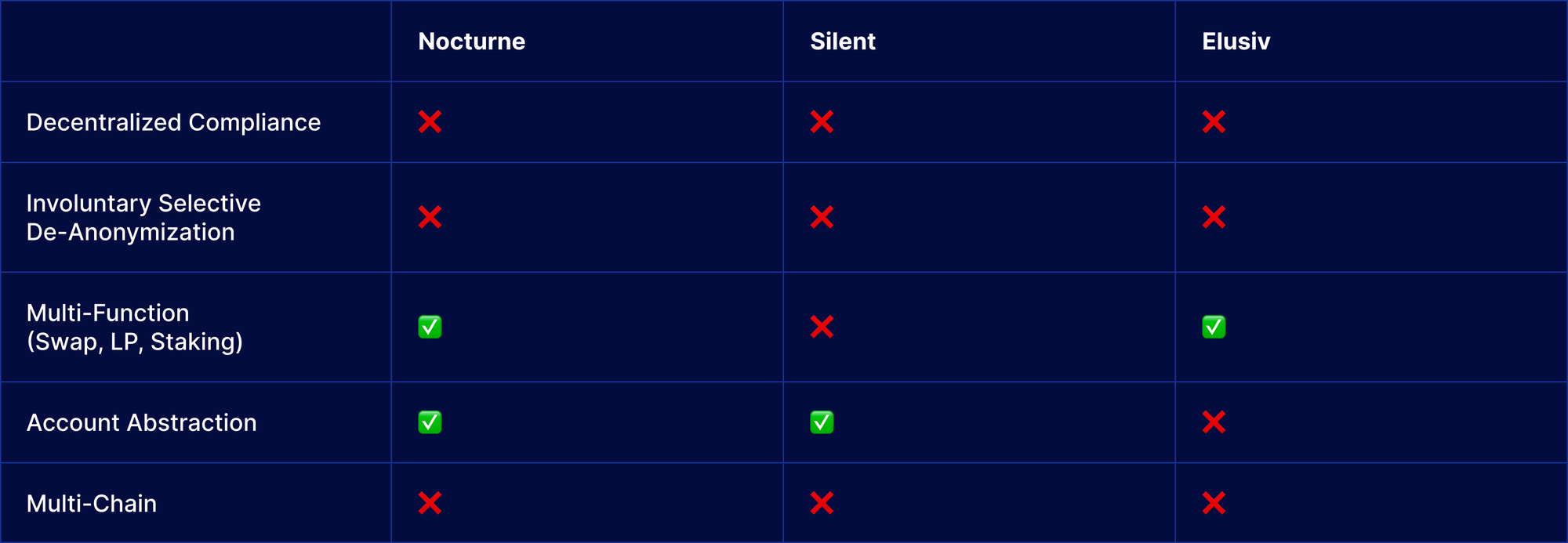
Missing piece of compliance in the privacy landscape
Till now, some privacy protocols have implemented basic compliance measures to prevent illicit activity. For example, Aztec’s zk.money and Tornado Nova imposed deposit limits to reduce the risk of illicitly obtained assets entering the system. Some protocols block addresses associated with government-sanctioned entities.
However, these methods often fail to provide robust compliance while protecting user privacy. Malicious actors can still exploit privacy-preserving applications, highlighting the need for more comprehensive and user-friendly solutions.
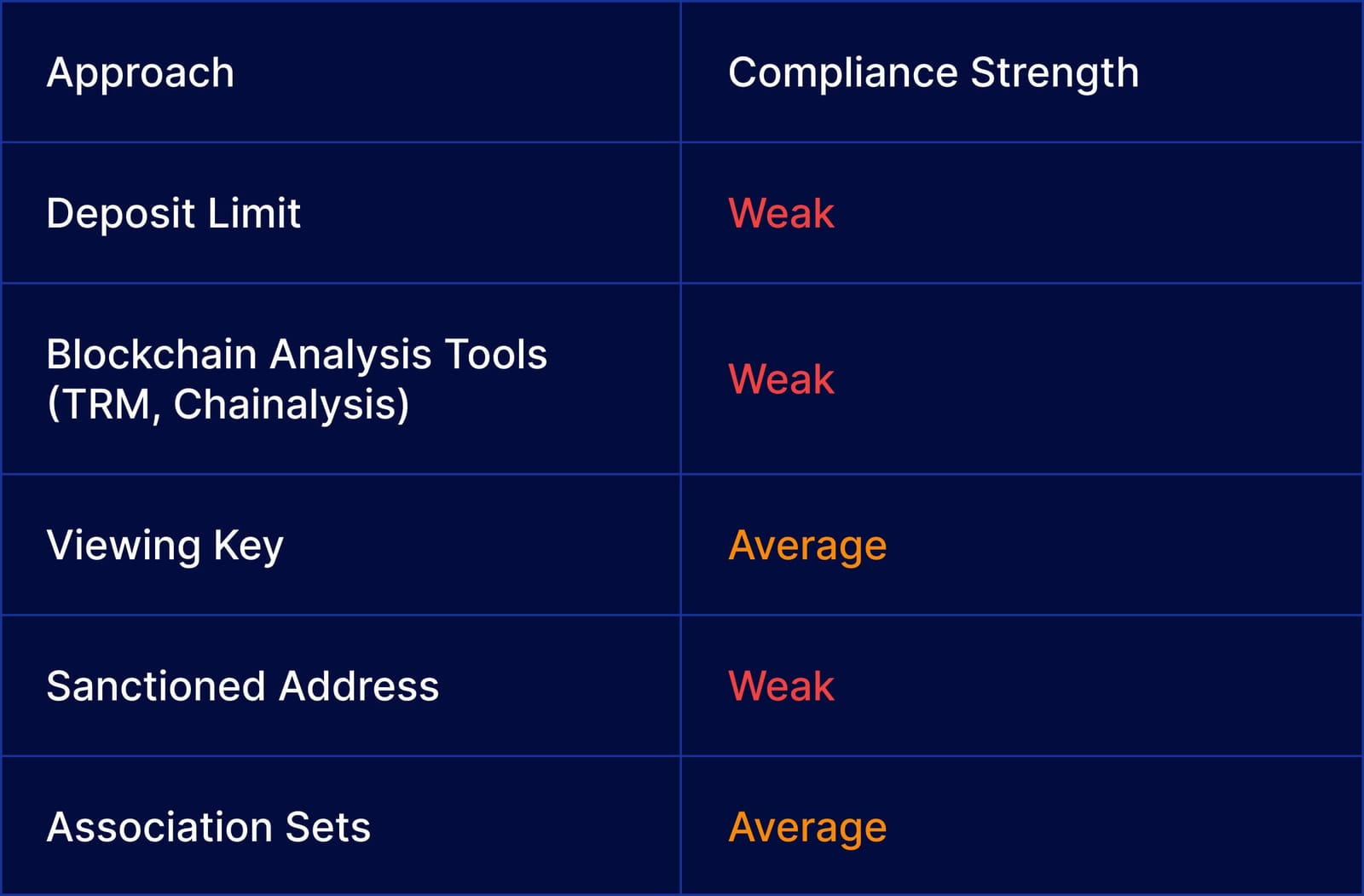
Compliance Comparison
Various compliance measures have been attempted, each with its limitations:
- Deposit Limits: While effective at deterring illicit use, limits inconvenience legitimate users and restrict use cases.
- Sanctioned Address Blocking: While regulators maintain lists of illicit addresses, malicious actors can bypass restrictions by transferring funds to new addresses before they are flagged.
- Blockchain Analysis Tools: While tools like Chainalysis and TRM Labs track illicit transactions, they can produce false negatives, making enforcement inconsistent.
- View-Only Access: Some applications offer view-only access keys that users can voluntarily share with regulators, but this approach lacks enforcement for malicious actors.
- Association Sets: Privacy pools, a concept proposed by Ameen Soleimani and Vitalik Buterin, allow users to associate with a subset of “good” deposits. However, delays in detecting illicit activity may still result in legitimate users being linked to flagged transactions.
While these compliance measures address some concerns, none fully resolve the privacy-compliance dilemma.
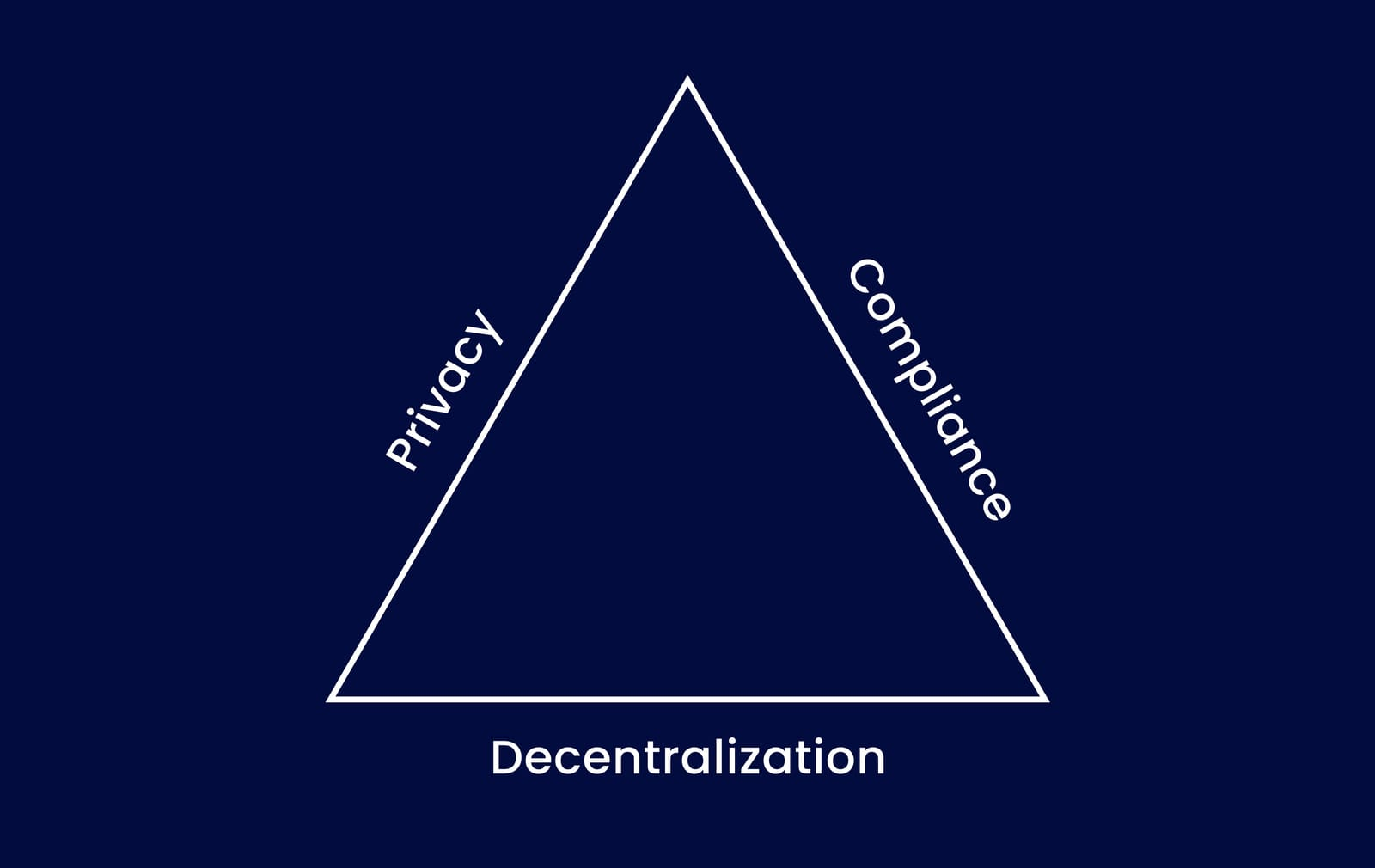
Labyrinth: Bridging the Privacy-Compliance Gap in a Decentralized Design
The blockchain industry has long struggled with the privacy trilemma—balancing privacy, compliance, and decentralization. Achieving all three has been a challenge. Labyrinth solves this problem by integrating privacy with regulatory compliance in a decentralized manner.
Key Features of Labyrinth
Labyrinth addresses the critical need to harmonize privacy and compliance in Web3. It does more than just protect transactions; it ensures privacy while maintaining regulatory compliance, setting the foundation for a trusted and decentralized financial system.
Prioritizing Privacy
Labyrinth places privacy at the core of its architecture. Using Zero-Knowledge Proofs (ZKPs), Labyrinth allows users to make private transactions while keeping their financial data confidential. This enables secure interactions across DeFi, payments, DAOs, social networks, and AI models. Labyrinth envisions a future where privacy is a fundamental right, not a luxury in the decentralized world.
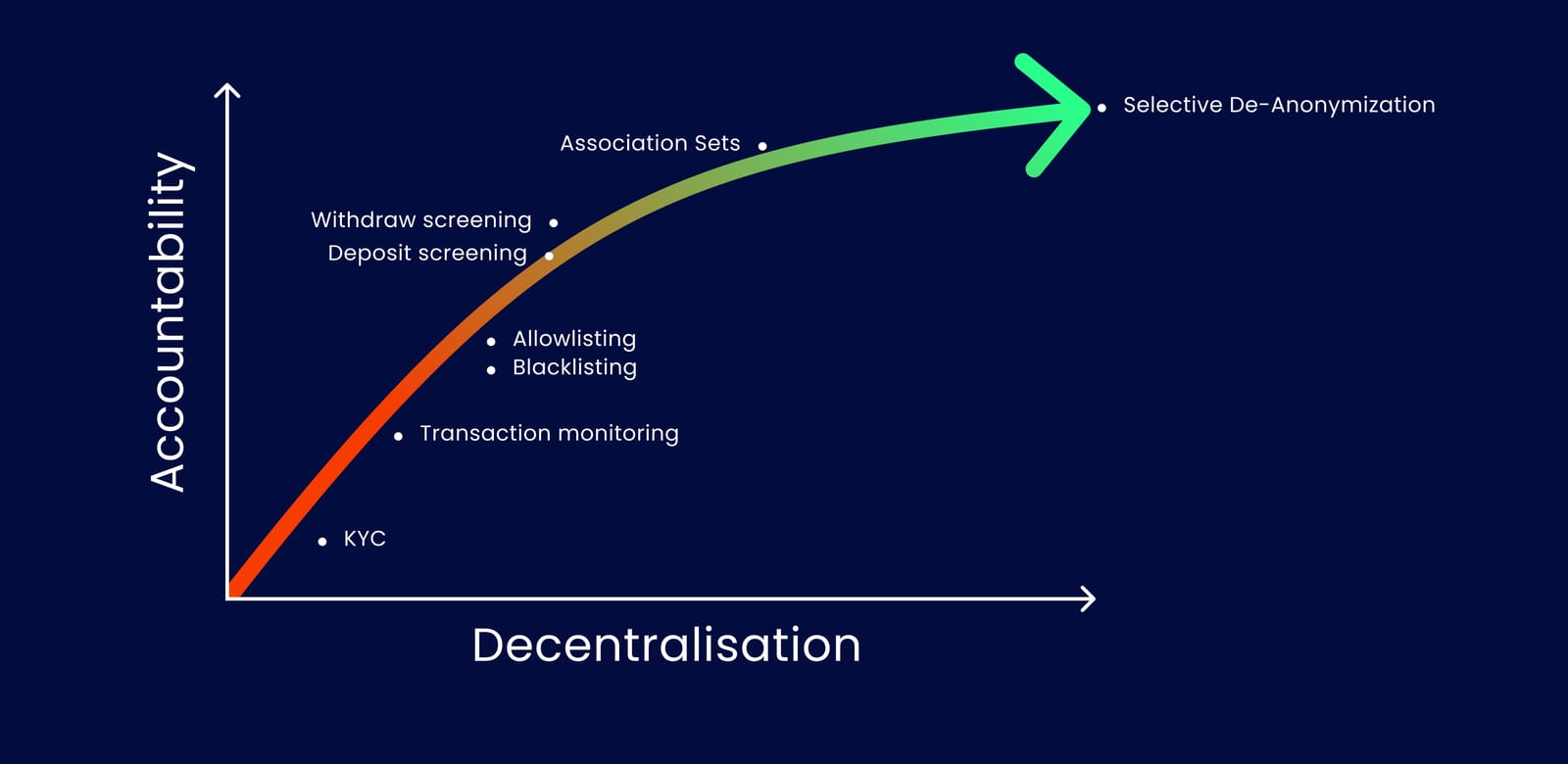
Decentralized Compliance
Labyrinth embeds compliance within its framework. It introduces Selective De-Anonymization (SeDe), which allows users to prove data ownership and selectively reveal transaction details if required. This approach ensures compliance without central control. Users can securely share verification keys with legal or tax authorities only when needed, allowing for a compliant yet privacy-first system.
For deep technical details, read our whitepaper.
Labyrinth SDK: A Decentralized Middleware Solution
Labyrinth offers an easy-to-integrate SDK for developers. This privacy middleware simplifies the adoption of privacy and compliance in Web3 applications.
Key Features of the Labyrinth SDK
- Private Payments via Stealth Addresses: Users receive assets through unique, random addresses for enhanced privacy.
- Shielded Wallets for Protocol UIs: Wallets can integrate privacy settings directly within interfaces like MetaMask Snaps.
- Multi-Chain Support: Ensures cross-chain compatibility, allowing seamless privacy across different blockchains.
Read more about SDK here.

Enabling Compliant Privacy for All
Labyrinth serves a broad range of Web3 use cases, providing a balance between security, compliance, and decentralization.
Privacy-Preserving DeFi
Labyrinth enables DeFi protocols to offer private transactions natively without disrupting their functionality.
- Aave: Users can borrow and lend privately, ensuring their financial activity remains hidden.
- Uniswap: Traders can swap tokens without exposing transaction history.
- Lido Finance: Users can stake assets while keeping their portfolio information confidential.
- User Wallets: Wallet providers like MetaMask, Coinbase, and Rainbow can integrate Labyrinth to provide a seamless private finance experience.
AI and Data Privacy
- Private AI/ML Interactions: Ensures that sensitive user data stays protected when interacting with on-chain AI models.
- Data Ownership & Monetization: Users can prove and monetize ownership of their contributions to AI models.
Privacy for Decentralized Social Platforms
- Full Control Over Data: Users can decide who sees their content and transactions.
- Data Monetization: Users can earn from their content while maintaining a private user experience.
Conclusion
Privacy, compliance, and usability are essential for the next phase of blockchain innovation. Labyrinth is pioneering Web3 privacy solutions that allow users, developers, and institutions to operate securely and legally.
Explore the whitepaper for technical insights and review research for compliance papers.
Labyrinth testnet is launching soon, and mainnet is coming next. If you are a developer or institution looking to integrate Labyrinth, explore our documentation or contact us at contact@labyrinth.ac.
Stay updated on Twitter/X.

